Risk Evaluations
When you define authentication or other flows for your users, you can include risk evaluations at relevant points in the flow. The risk evaluation that is carried out is based on the risk policy that you specify for the evaluation. The following diagram shows a simplified sample flow that includes risk evaluation.
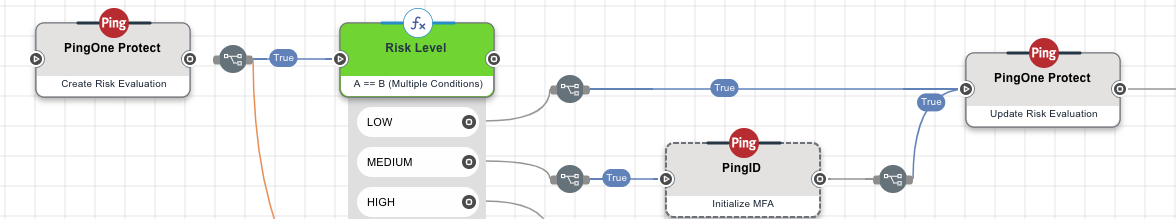
Note that the flow includes two distinct steps relating to risk evaluation.
The actual risk evaluation step should be added at a point in the flow where you would like to base the next action on the risk level calculated, for example, show an MFA prompt for medium or high-risk, but automatically grant access if the risk is deemed to be low.
After completion of the authentication steps, your flow should include a step to update the risk evaluation system with the results of the flow - was authentication completed successfully.
To ensure protection against fraudulent access attempts, it is essential that your flows include the SUCCESS/FAILED update step to indicate whether the flow was completed successfully or not. Many of the predictors used in risk policies are based on gradual learning of the characteristics of the access attempts made by your users, for example, where were they physically located and what operating system were they using. This learning process can only take place if your flows provide a clear indication which access attempts were made by legitimate users.
Risk evaluation data model
| Property | Type | Required? | Mutable? | Description |
|---|---|---|---|---|
|
Date |
N/A |
Read-only |
The time the resource was created (format ISO-8061). |
|
Object |
Optional |
Mutable |
Contains additional information about the risk evaluation. Refer to the following Details data model table. |
|
String |
Required |
Immutable |
The environment resource’s unique identifier. |
|
Object |
Required |
Mutable |
Contains the attributes identifying the event. For more information about event attributes, refer to the following Event data model table. |
|
String |
N/A |
Read-only |
The risk evaluation’s unique identifier. |
|
String |
Optional |
Mutable |
The risk policy set’s unique identifier. If this property and |
|
String |
Optional |
Mutable |
The risk policy set associated with this name. If this property and |
|
Boolean |
Optional |
Immutable |
Set |
|
Object |
N/A |
Read-only |
Contains the risk policy that evaluates as |
|
String |
N/A |
Read-only |
The risk evaluation result level. Options are |
|
String |
N/A |
Read-only |
The recommended course of action based on the evaluation. Currently used only for policies that include a bot detection predictor, an Adversary-in-the-Middle (AitM) predictor, an email reputation predictor, or a traffic anomaly predictor. If
|
|
String |
N/A |
Read-only |
The risk evaluation result type. Options are |
|
Date |
N/A |
Read-only |
The time the resource was last updated (format ISO-8061). |
Event data model
These properties specify information about events processed for risk evaluation.
|
The |
| Property | Type | Required? | Mutable? | Description |
|---|---|---|---|---|
|
String |
Optional |
Mutable |
To improve risk analysis, provide the value of a persistent cookie. |
|
String |
Optional |
Mutable |
The user agent string for the browser. |
|
String |
N/A |
Read-only |
Whether the flow completed successfully. For the various flow types,
|
|
Object |
Optional |
Mutable |
Contains information about the device being used. |
|
String |
Optional |
Mutable |
If you want to maintain your own device IDs, you can send the device ID to the risk evaluation by using |
|
String |
Optional |
Mutable |
The state of the transaction. Options are |
|
String |
Optional |
Mutable |
The transaction type. |
|
String |
Optional |
Mutable |
The type of flow for which the risk evaluation is being carried out. Can take any of the following values:
The default value is |
|
String |
Optional |
Mutable |
If you want to provide additional detail about the context of the flow, you can specify a subtype in addition to
|
|
String |
Required |
Mutable |
The originating IP address of the authentication flow. |
|
String |
Optional |
Mutable |
The calling service. |
|
Object |
Optional |
Immutable |
Object used to provide the data from the Signals (Protect) SDK. |
|
String |
Optional |
Immutable |
The data collected by the Signals (Protect) SDK. |
|
String |
Optional |
Mutable |
The unique session ID associated with the event. |
|
String |
Optional |
Mutable |
Whether a device is likely used by a single individual, or shared among multiple users. Used to adjust risk interpretation and risk policy decisions. If not specified, risk engines may over-penalize normal behavior on shared devices, or under-estimate risk on private devices. Options include |
|
String |
Optional |
Mutable |
The unique identifier representing the application, service, or resource the user is attempting to access or act upon. This identifier is used for policy targeting, analytics, and consistent risk evaluation. For PingOne integrations, this value corresponds to the PingOne application ID. For non-PingOne integrations, define this value and ensure it is unique within your environment. |
|
String |
Optional |
Mutable |
The name describing the target application or resource. This name is intended for display, logging, and explainability purposes. The name does not need to be unique, and may change over time without affecting policy behavior. |
|
String[] |
Optional |
Mutable |
The list of groups the user belongs to, representing organizational, role-based, or business-level classifications associated with the user. Groups can be used as contextual signals for authorization, policy evaluation, risk assessment, and fraud detection. They allow decisions to be tailored based on the user’s role, privileges, or segment within an organization. |
|
String |
Optional |
Mutable |
The name of a group associated with the user. Group names may represent roles, departments, access levels, or other organizational classifications. |
|
String |
Optional |
Mutable |
A unique, persistent identifier for the user that remains constant across events and time. This ID enables identity correlation, historical analysis, and consistent risk evaluation. For |
|
String |
Optional |
Mutable |
A human-readable identifier for the user, typically the username or login identifier (for example, an email address). |
|
String |
Required |
Mutable |
The type of user associated with the event. The possible values are |
Details data model
A POST request returns the following attributes in the details property for the specified event.
| Property | Type | Required? | Mutable? | Description |
|---|---|---|---|---|
|
Boolean |
N/A |
Read-only |
Indicates whether the current authentication originated from an anonymous network (for example, proxy or VPN). |
|
String |
N/A |
Read-only |
The city related to the current transaction from the IP address. |
|
String |
N/A |
Read-only |
The country related to the current transaction from the IP address. |
|
Object |
N/A |
Read-only |
Relevant only for Bot Detection predictors and Suspicious Device predictors. Contains the information on the rule that led to the |
|
Integer |
N/A |
Read-only |
Relevant only for Bot Detection predictors and Suspicious Device predictors. ID number of the rule that led to the |
|
Object |
N/A |
Read-only |
Contains information about the device being used. |
|
Object |
N/A |
Read-only |
For risk evaluations that include the PingID Device Trust predictor, contains the data from the trust agent. |
|
Integer |
N/A |
Read-only |
If a local script was specified when installing the Workforce Trust agent on individual computers, will contain the exit code for the script. |
|
String |
N/A |
Read-only |
If a local script was specified when installing the Workforce Trust agent on individual computers, will contain the output of the script. |
|
String |
N/A |
Read-only |
The ID generated by the agent to identify the user’s computer. |
|
String |
N/A |
Read-only |
The domain name for the logged-in user. |
|
String |
N/A |
Read-only |
The name of the logged-in user. |
|
String |
N/A |
Read-only |
The SID (security identifier) for the logged-in user. |
|
Array |
N/A |
Read-only |
The MAC addresses of the user’s computer. |
|
String |
N/A |
Read-only |
The name of the user’s computer. |
|
String |
N/A |
Read-only |
The operating system on the user’s computer. |
|
String |
N/A |
Read-only |
The version of the operating system on the user’s computer. |
|
String |
N/A |
Read-only |
The version of the trust agent. |
|
Double |
N/A |
Read-only |
The distance between the current location of the device and the location of the device when the last risk evaluation was carried out. Distance is given in meters. |
|
String |
N/A |
Read-only |
The externally-maintained device ID that was provided in the risk evaluation request, if such an ID was included. For more details, refer to the Event data model. |
|
Date |
N/A |
Read-only |
If an externally-maintained device ID was provided in the risk evaluation request, |
|
String |
N/A |
Read-only |
The device ID provided by the Signals (Protect) SDK. |
|
Date |
N/A |
Read-only |
The date and time the device was last seen. Returned only if the risk policy used for the evaluation includes the New Device predictor. |
|
Double |
N/A |
Read-only |
The distance between the user’s current location and the user location when a risk evaluation was last updated with the completion status |
|
Integer |
N/A |
Read-only |
The speed the user would have had to travel at to reach their current location, based on the distance from the location when a risk evaluation for the user was last updated with the completion status |
|
Boolean |
N/A |
Read-only |
Indicates whether the distance between the location of the user in their previous successful authentication and current authentication infers that the user had to travel at a speed greater than 1000 kilometers per hour. This condition is marked as fulfilled, only if:
|
|
Integer |
N/A |
Read-only |
The autonomous system number. |
|
String |
N/A |
Read-only |
The ISP that registered the domain. |
|
String |
N/A |
Read-only |
The organization that owns the domain. |
|
String |
N/A |
Read-only |
The second-level domain. |
|
String |
N/A |
Read-only |
The top-level domain. |
|
String |
N/A |
Read-only |
The risk level of the evaluated IP address. Options are |
|
Integer |
N/A |
Read-only |
Represents the calculated score of the IP address involved in the transaction. Scores range between 0 and 100. A score of 0 indicates a non-risky IP address; a score of 100 indicates a high-risk IP address. If the IP address reputation score is not available for the specific IP address, |
|
Boolean |
N/A |
Read-only |
Indicates whether an anonymous network was detected. Information is available twenty-four hours after the last successful transaction. |
|
String |
N/A |
Read-only |
The city of the IP address involved in the transaction. Information is available twenty-four hours after the last successful transaction. |
|
String |
N/A |
Read-only |
The country of the IP address involved in the transaction. Information is available twenty-four hours after the last successful transaction. |
|
String |
N/A |
Read-only |
The IP address involved in the transaction. Information is available twenty-four hours after the last successful transaction. |
|
String |
N/A |
Read-only |
The state of the IP address involved in the transaction. Information is available twenty-four hours after the last successful transaction. |
|
String |
N/A |
Read-only |
The timestamp of the transaction. Information is available twenty-four hours after the last successful transaction. |
|
String |
N/A |
Read-only |
The state or province related to the current transaction from the IP address. |
|
String |
N/A |
Read-only |
The risk score calculated for the predictor-related transactions associated with the accessing device, and for the current authentication attempt. Options are |
|
String |
N/A |
Read-only |
The reason (or reasons) provided for the risk score classification (for example, the operating system or browser type used by the device, and country in which the accessing device is located). Each reason is classified as Unusual, to indicate how much it deviates from normal user behavior, and its effect in calculating the overall predictor risk score. Note that these messages may change in the future. If you want to take action based on a certain scenario, the action should be based on the value of |
|
String |
N/A |
Read-only |
Additional information about the predictor evaluation outcome. Example responses are |
|
String |
N/A |
Read-only |
The type of the predictor. |
Update Risk Evaluation data model
| Property | Type | Required? | Mutable? | Description |
|---|---|---|---|---|
|
String |
Required |
Immutable |
If the flow was completed successfully, set to |
Risk evaluations events generated
Refer to Audit Reporting Events for the events generated.
Response codes
| Code | Message |
|---|---|
200 |
Successful operation. |
201 |
Successfully created. |
400 |
The request could not be completed. |
401 |
You do not have access to this resource. |
403 |
You do not have permissions or are not licensed to make this request. |
404 |
The requested resource was not found. |
Providing feedback for risk evaluations
Use the riskFeedback endpoint to provide feedback on the accuracy of specific risk evaluations that were carried out. The request for providing feedback takes a list of feedback items, each consisting of the risk evaluation ID, a feedback category, and a reason for including it in that category (optional). In each such request, you can include feedback for up to 100 risk evaluations.
Risk evaluation feedback data model
| Property | Type | Required? | Mutable? | Description |
|---|---|---|---|---|
|
Array |
Required |
Immutable |
The collection of feedback items. |
|
String |
Required |
Immutable |
One of the following categories of feedback: |
|
String |
Optional |
Immutable |
The reason that the specific feedback category was specified. The possible values depend upon the category chosen.
|
|
Date |
Optional |
Immutable |
The date and time the risk evaluation was carried out. Use ISO-8061 format, for example, |
|
String |
Required |
Immutable |
The ID of the risk evaluation. |
Below is the sample body for a request that provides feedback on three risk evaluations. Full sample request can be found here.
{
"evaluationFeedbackItems":[
{
"riskEvaluation": {
"id": "15f1d245-33b3-4dba-849d-4df4b64b2d42"
},
"feedbackCategory": "FRIENDLY_BOT",
"reason": "INTERNAL_AUTOMATION"
},
{
"riskEvaluation": {
"id": "d1b638b4-638e-4c56-8fc6-872691c1bab1"
},
"feedbackCategory": "FALSE_HIGH_RISK",
"reason": "COMPANY_VPN"
},
{
"riskEvaluation": {
"id": "35f1d245-33b3-4dba-849d-4df4b64b2d45"
},
"feedbackCategory": "FALSE_HIGH_RISK"
}
]
}