What is Model Context Protocol (MCP)?
The foundational challenge in scaling agentic systems is managing the connections between artificial intelligence (AI) agents and the vast array of tools they need to perform their work.
To solve real-world problems, AI agents require connections to external data and services, such as APIs and databases. Without a common standard, each integration must be written and maintained separately, creating brittle connections and duplicated effort. This approach doesn’t scale, especially when multiple agents use the same tools.
The Model Context Protocol (MCP), developed by Anthropic, addresses this challenge by standardizing how agents connect to tools. By providing a consistent layer for agent-tool interaction, MCP reduces friction for developers, simplifies maintenance, and creates a foundation for interoperable, secure agent ecosystems.
Key benefits
MCP’s standardized integration layer delivers:
-
Consistent connection semantics: Developers can swap in a new tool without rewriting core integration logic.
-
Secure authentication and authorization: MCP servers support OAuth 2.0, eliminating the need for hard-coded secrets or long-lived credentials.
-
Capability discovery: Agents can automatically discover available tools, resources, and prompts instead of relying on hard-coded lists.
-
Reduced duplication: Multiple agents can reuse the same MCP server, reducing the operational burden of maintaining separate connectors.
Architecture
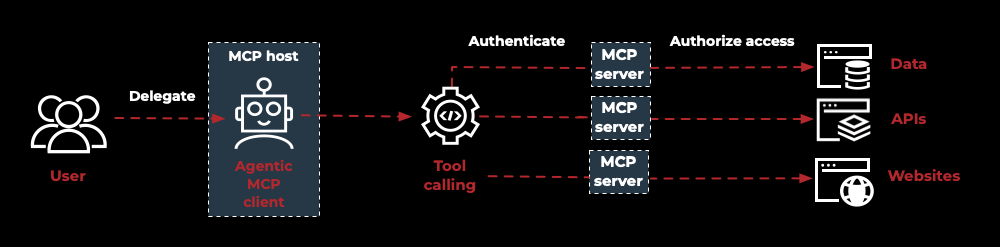
The MCP architecture includes three core components:
- MCP host
-
The application that manages MCP clients and initiates connections to MCP servers. It provides the environment in which agents operate and interact with tools and resources. For example, an AI-powered IDE.
- MCP client
-
The component inside the host that maintains a standardized connection with the MCP server. It acts as a bridge between the agent’s reasoning and the server’s tools, resources, and prompts. The client translates agent requests into MCP-compliant messages and processes server responses in a consistent way. For example, an embedded IDE client or chatbot agent connector.
- MCP server
-
A program that exposes capabilities to AI applications in a standardized and discoverable way. It acts as the central repository of tools, resources, and prompts that agents can invoke. MCP servers support OAuth 2.0 for authentication and authorization, ensuring secure access, and can run locally within a host or remotely as a centralized service.
An MCP server can expose three main types of capabilities:
-
Tools: Executable functions that an agent can invoke to perform specific actions.
-
Resources: Contextual data that informs agent reasoning, such as files, database records, or configuration information.
-
Prompts: Pre-defined, templated messages or workflows that agents can present to users or use internally to structure reasoning.
-
MCP’s technical architecture is based on the JSON-RPC 2.0 message format. This ensures that all interactions, such as tool invocation, resource retrieval, and prompt execution, follow a consistent pattern. Each message contains a unique identifier, method name, and parameters.
Workflow
A typical MCP workflow unfolds as part of an agent’s reasoning-action loop:
-
Initialization: The MCP host launches an MCP client, which connects to the MCP server. The client queries the server for available tools, resources, and prompts. The agent inspects this metadata to understand which capabilities are available before taking action.
-
Invocation: When the agent determines that a specific tool or resource is needed, the MCP client sends a JSON-RPC request to the server, specifying the method and any required parameters.
-
Execution: The server applies authentication and authorization checks using OAuth 2.0 and least-privilege scopes, ensuring the client is permitted to execute the requested action. The server then performs the requested operation.
-
Response: Results are returned in a standardized JSON-RPC response. If an error occurs, the response includes a structured error object. The client relays the results to the agent, which incorporates them into its reasoning.
-
Iteration: Based on the results, the agent might issue additional MCP requests, chaining tool calls or resource queries to achieve higher-level goals. This iterative process allows the agent to refine its reasoning and dynamically adapt to changing conditions or new data.
-
Observability & Logging (Optional): Hosts or clients might log requests, responses, and execution traces to support debugging, auditing, or performance monitoring.
In the following example, an agent is connected to a support team’s ticketing system. The MCP server exposes a tool called searchTickets, which lets agents query tickets by status, assignee, or other fields.
Suppose a support agent makes the following query to an AI agent:
Show me all my open tickets.
The LLM then processes this request and makes the following MCP call:
{
"jsonrpc": "2.0",
"id": 1,
"method": "searchTickets",
"params": {
"status": "open",
"assignee": "me"
}
}-
method: The MCP tool being called (searchTickets) -
params: The query parameters for filtering tickets
The MCP server returns a structured list of open tickets:
{
"jsonrpc": "2.0",
"id": 1,
"result": [
{
"ticketId": "123",
"title": "Login issue",
"priority": "high"
},
{
"ticketId": "124",
"title": "Billing discrepancy",
"priority": "medium"
}
]
}The agent acting as the MCP client can now summarize tickets for the user, suggest next steps, or chain further requests by calling other MCP tools.
Security challenges
While MCP streamlines tool integration, it also introduces new identity and security challenges. Each MCP server must enforce strong authentication and authorization to ensure only trusted clients can access tools and resources.
Common security challenges include:
-
Configuring OAuth 2.0 correctly to avoid reliance on static secrets
-
Implementing least-privilege scopes so agents can only access the data they need
-
Securing multi-tenant MCP servers with fine-grained access control to prevent data leakage across users
-
Protecting against denial-of-service with unbounded tool calls, and mitigating risks from prompt injection that could trigger malicious tool execution
Learn more about MCP security best practices in MCP servers and OAuth 2.0.